Safe Browsing for Normal People
More digital defense advice from the old geek on the porch in his rocking chair
Your WiFi connection may not be safe
You’re in your favorite coffee shop, FourBucks, and while enjoying a delicious caffeinated beverage, you decide to check your bank account to see if your latest paycheck has been deposited yet. Nope, not today. Oh well, the coffee is gone, so it’s back to work.
Checking again the next morning, you are horrified to discover that the entire contents of your bank account is gone. How could this happen? You have a 14-character password, that you change more often than your socks. It must have been a bank employee. I feel your pain, but don’t blame your bank. You may have actually seen the crook. Remember that shifty-looking guy in the corner, hunched over a laptop? That’s him in the photo above.
He never came near you, so there’s no way he got your login information by looking over your shoulder. He didn’t need to. The cellular Internet in that coffee shop is really slow, so you use their WiFi. Your phone may have popped a warning about it being an unsecured connection, but you ignored that.
An unsecured connection is like a postal system where every piece of mail is a postcard. Your postman can read any and all of your mail before putting it in your mailbox. Likewise anyone with the right software can intercept all of the data being sent back and forth through WiFi, and save it for later analysis.
The laptop that the dodgy dude was using might also contain special software that tells the world it is a free WiFi access point. When you connect, it grabs all the data you send online, stores it, and then forwards the data to the site you sent it to. Everything seems perfectly fine, but in the process you have given him the website of your bank and all the data needed to log in. This is called a Man in the Middle attack. It’s like the note system used by middle school students, where the person to your right gives you a note to pass to the person on your left.
There are two easy ways to block this type of attack. The first is to not use the local WiFi at all, but rather use a cellular data connection. Cellular data connections are encrypted and secure. Your phone provider ensures this so they can measure how much data is being used, and charge you accordingly.
A second way is to use a VPN. This is similar to the Man in the Middle process, except that the middleman is a secure server that your VPN software uses.
VPN stands for Virtual Private Network. It encrypts everything you type in your browser, sends it to a special server that decrypts and forwards the data to the intended destination. Note that the data leaving the VPN server will also be encrypted as long as it is going to a secure website. Web connections use HyperText Transfer Protocol, a universal system for sending text between computers. That’s why website addresses begin with http. If you are connecting to a secure website, the prefix is https:// instead of http://, the data is encrypted and secure for the round trip. Only very old websites will still be using the unsecured connection, and your browser will almost certainly warn you about that. Most browsers confirm that you are on an encrypted connection by putting a small padlock icon in the address bar.
Security is only one feature offered by a VPN. Because all of your requests go to the VPN server to be sent on to the final destination site, the receiving site uses the location data from the VPN server to determine where you are. This, along with the encryption, is very helpful for people living under repressive governments that restrict what they can say, and to whom they can say it. VPNs are also sometimes used by folks who want to use services that are restricted to residents of a particular area. For example, someone in Weeping Willow, Nebraska, that wishes to view video streams from the United Kingdom, can use a VPN to make it look like they are in the UK.
Many different companies are now offering VPN software for everyday use. The ads are sometimes deceptive. Typically they stress that using a VPN will give you security from government or criminal spying on what sites you visit, or what emails you get. It won’t prevent companies from tracking you, and it won’t keep malware out of your computer. Having a VPN is like having a very secure deadbolt lock on your front door, while several windows are open. It’s a good start, but you can do more.
Be careful when buying VPN software. Some of the well-known companies are ExpressVPN, NordVPN, and ProtonVPN. They don’t keep copies of the data that they transfer, and the companies themselves are located outside of the US. That allows them to decline governmental requests to tap into your transmission data. While most of these companies offer a short free trial, any VPN software that is free, or very low cost, may actually be offered by criminal enterprises. By acting as your VPN they can collect your data while pretending to protect it.
You Are Being Tracked
You’ve probably heard about cookies. Not the ones made by elves in a hollow tree, but very small data files that get planted on your computer by just about every site you visit. Some are beneficial. For example, when you log into a site frequently, and you check the Remember Me box. When you visit the site the next time, it looks for a cookie that was set before, and it knows who you are. But there are other cookies that are markers used to identify you. They are sold to data brokers, who in turn make profiles. Those profiles are valuable to advertisers, so they can target you with products and services that match the interests they know you have.
There’s also Google, and the other search engines. Nearly all of them keep a record of what you have searched for. Clearing your search history has no effect on that. Search for a new barbecue grill, then go check the weather. You’ll find that many of the endless ads you encounter on the weather site are for barbecue grills. This is also true of Facebook, whose very business model is built on getting as much detail as possible about you and selling it to advertisers. Let’s not forget about Amazon, who knows every single item you ever bought from them. They even know when you’re running out, so they can send you a reminder.
Perhaps you already knew you were being tracked. You didn’t think much about it, because you’re a good person who has nothing to hide. But the data brokers are not interested in your character, only in who they can sell you to. Some of their customers are not businesses trying to sell you things, but criminals who are looking for targets to swindle.
The only way to keep your data to yourself is to live in a cabin deep in the woods with no Internet. If you’re reading this I’m afraid it’s too late for that. While a VPN will not block tracking, there are some things you can do. Most web browsers now have settings that allow you to block cross-site tracking. That’s what it’s called when site A puts a cookie in your computer, and then shares it with sites B, C, and D. So when you browse a site offering sports clothing, they plant a cookie. Visit the running shoe site, and they use that cookie to know what you were looking for, and what your tastes are.
You can defeat cookies, to some extent, by browsing in Private mode. That disables most tracking, and does not keep a history of what sites you have visited. Various browsers, such as Apple Safari, also have option settings to limit how much tracking can be done. There are also browser extensions that can prevent unintentional data leakage.
Here are two search services that do not track what you search for, or keep a history of your searches:
DuckDuckGo is a good search engine, and it does not track you at all. You may see ads in the results, but they are targeted based on what you searched for, not any trackers planted in your computer. By selling ads the site makes enough money to keep it free for your use.
Ecosia also does not track you, and they are helping the environment. A portion of the revenue they make from ads is used to plant trees. They have planted more than 200 million trees all over the world.
Browser Attacks
A favorite technique of criminals trying to trick you is by providing a link to a site that they control. You may get this link in an email, a text message, or maybe even from someone on a phone call. It’s important to understand that a site may look exactly like your bank or credit card company, right down to the logos and fonts. It’s very easy for criminals to do that.
Large companies, like Amazon, Apple, and Microsoft, have many servers in very secure locations. A staff of experts is on hand to keep them running securely. Some small- and medium-sized businesses may host their websites on their own servers, using off-the-shelf software that is inexpensive, or even free. Typically such servers are not well-secured, and a skilled hacker can gain access to install their own content. Usually the site owner is completely unaware of the breach. Once hackers gain access, existing website code can be modified to trick unsuspecting users.
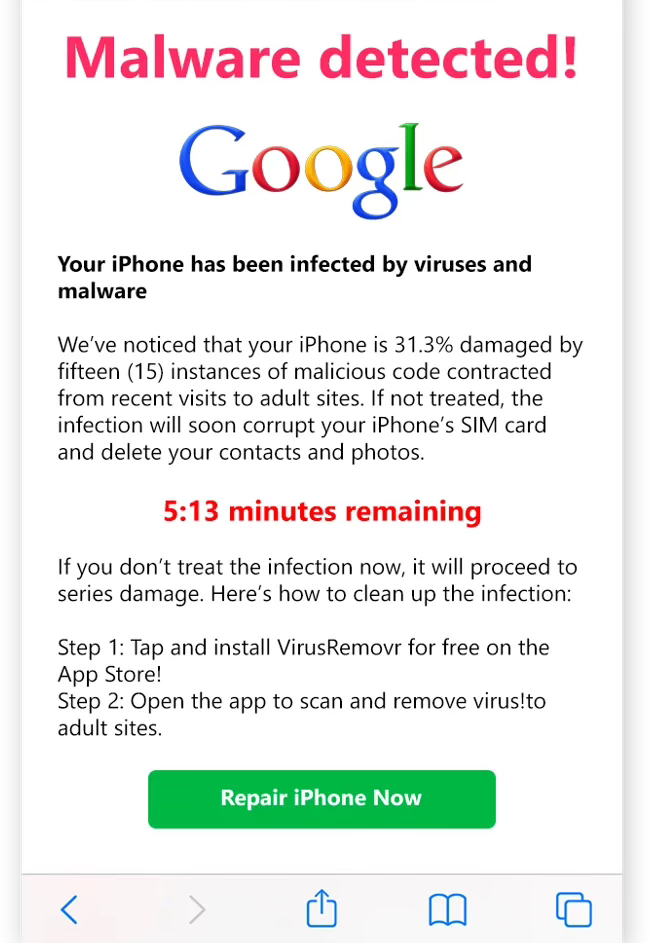
To understand this type of attack, let’s walk through an example. You’re spending a relaxing weekend catching up on your favorite sites. Suddenly a message pops up, covering almost the entire screen. It screams A virus has been detected! and has a prominent button labeled Remove the Virus. At the same time there is the sound of a siren coming out of your speaker. Trying to close the browser window has no effect. What to do?
We’ll start with what you should not do. Don’t click on any buttons or link inside that message. The whole idea is to get you to panic, and frantically click the button. That will lure you into entering information that will allow the fake virus message to infect your computer with real malware. Some variations of this attack may contain a phone number, supposedly for Apple or Microsoft. If you call the number, the person answering will direct you to a website which can lead you to self-install the malware. None of the computer or software companies have a number you can call for help with a virus.
You can try to close the browser window, but that may not work. Close any other windows you have open to save your work, and then restart the computer. If you are using Windows, you almost certainly have anti-virus software in use, such as the included Windows Defender. How did it miss this virus? Well it most likely did not miss it, because the message is fake. It was actually a carefully crafted message sent as a notification. It’s very common for a site to ask your permission to send you notifications. The purpose is to alert you to new products, features, or events. If you allow notifications, and the website is later compromised, it allows the hacker to send notifications to your computer that look like virus alerts. It may even match the logo and wording of the anti-virus software you are using.
In the Safari browser that I use, it’s possible to change settings to allow or deny notifications from specific websites. Other browsers should have the same capabilities, especially now that these types of attack are more frequent. It’s also possible to get this type of attack on a smartphone.
There are several clues that this is bogus. Google may be the default search engine on your phone, but it is not watching for virus or malware. Any sort of malware prevention software is not likely to be able to pinpoint exactly how many instances of malicious code are on the phone. And it’s not possible for software to corrupt a SIM card, though many phones now use an electronic SIM that could possibly be damaged. A search of the App Store reveals that VirusRemovr does not exist. Tapping the button will almost certainly take you to a specially crafted website that will extract information that will be used to steal from you.
This is not the end. As I write this, there are armies of people around the world working diligently to create better methods for separating you from your money. As new ones emerge I will post updates on Notes, and I will write one more article in this genre to talk about email scams. Be safe, live long, and prosper. Beam me up Scotty.